How do models help organisations assess their cybersecurity capabilities?
Evaluating the effectiveness of processes
In CYRUS, the project partner Cefriel developed the Cybersecurity Maturity Model for Educational Paths (CMM-EP) to identify gaps and needs in cybersecurity in the transport and manufacturing industry, which need to be addressed in the trainings developed in the project.
Tried-and-tested basis
It is based on the Capability Maturity Model (CMM), a framework used to assess and improve the maturity and effectiveness of processes within an organisation. Originally, it was developed in 1986 by the Software Engineering Institute (SEI), primarily for assessing and improving software development and software engineering processes. The model has been adapted and applied to various other domains and industries like project management and systems engineering.
“We used the Capability Maturity Model as a basis for our Cybersecurity Maturity Model for Educational Paths because it allows organisations to assess their current processes and identify areas for improvement easily,” says Andrea Guerini from Cefriel.
The CMM provides a structured approach for organisations to improve their processes, efficiency, product quality and overall performance. The key idea is to help organisations move from ad-hoc and unpredictable processes to well-defined, repeatable and optimised ones. Therefore, the CMM defines five maturity levels:
- Initial: Processes are ad hoc, reactive and unstructured. There is little to no process discipline, and success depends on individual efforts.
- Repeatable: Organisations start implementing basic project management and processes. Processes are documented on the project level and there is some level of consistency in their execution.
- Defined: Organisations have well-defined and documented processes. These processes are standardised and are consistently followed across the organisation.
- Managed: Organisations use quantitative data and statistical techniques to quantitatively manage, control and improve processes.
- Optimising: Organisations continuously strive for process improvement to achieve maximum effectiveness.
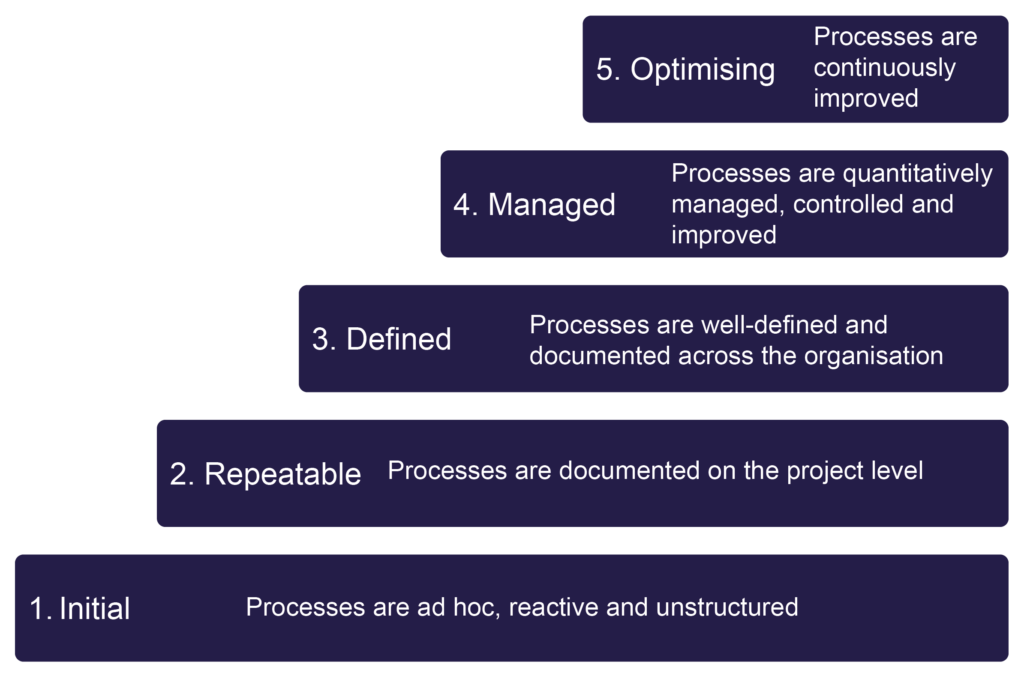
Capability Maturity Model (CMM)
By following the framework, organisations can gradually improve their processes and achieve higher maturity levels.
Evaluating the maturity of a company’s cybersecurity scope
Based on the CMM framework, Cefriel elaborated the Cybersecurity Maturity Model for Educational Paths (CMM-EP) as a crucial component in evaluating the maturity of a company’s cybersecurity scope. It is explicitly tailored to assess the training processes’ maturity and is used to categorise and analyse results more effectively.
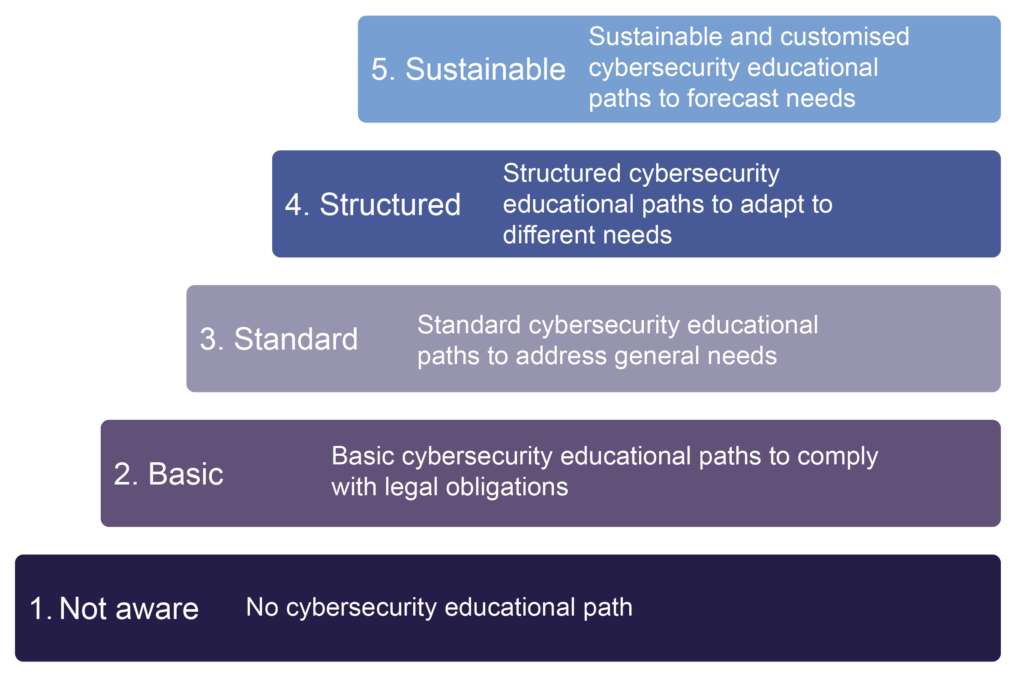
Basis of the Cybersecurity Maturity Model for Educational Paths
Each level describes the company’s capabilities:
- Level 1 – NOT AWARE: Organisations fail to prioritise cybersecurity learning paths, disregarding potential threats and neglecting to implement risk reduction activities. At this level, the efforts of organisations are inadequate, and their work remains highly exposed to threats.
- Level 2 – BASIC: Organisations have adequate diligence to barely comply with regulatory or legal requirements regarding cybersecurity education. They utilise off-the-shelf educational resources and provide them to their staff without customisation. At this level, cybersecurity capabilities are considered insufficient to address present and future scenarios properly.
- Level 3 – STANDARD: Organisations have implemented cybersecurity education programmes, but these programmes are mostly general and lack customisation. These organisations are beginning to encourage secure behaviours and improve their technical abilities in cybersecurity differently across departments. They have countermeasures for the most basic threats.
- Level 4 – STRUCTURED: Organisations prioritise structured cybersecurity education that caters to the evolving needs of both organisations and individuals. They measure progress and identify areas for improvement to enhance their security posture. Education is regarded as a critical tool to mitigate cyber risks and is closely tied to threat intelligence assessments. At this level, organisations are ready to cope with the most widespread global threats.
- Level 5 – SUSTAINABLE: Organisations integrate security-related values and educational pathways. They implement an all-encompassing cybersecurity educational strategy, deliver awareness and learning paths tailored to the requirements as well as continuously assess the outcomes. At this level, organisations can predict the impact of training activities on costs vs. risk reduction and adopt strategies that consider possible customised attacks that could undermine the business.
To evaluate these levels for an organisation more precisely, the Cybersecurity Maturity Model for Educational Paths assesses them in three different dimensions – the main elements of cybersecurity:
- Information & Operational Technologies,
- Processes,
- Technical & Cultural Level of People.
The combination of the five levels and the three dimensions results in the following matrix, the Cybersecurity Maturity Model for Educational Paths:
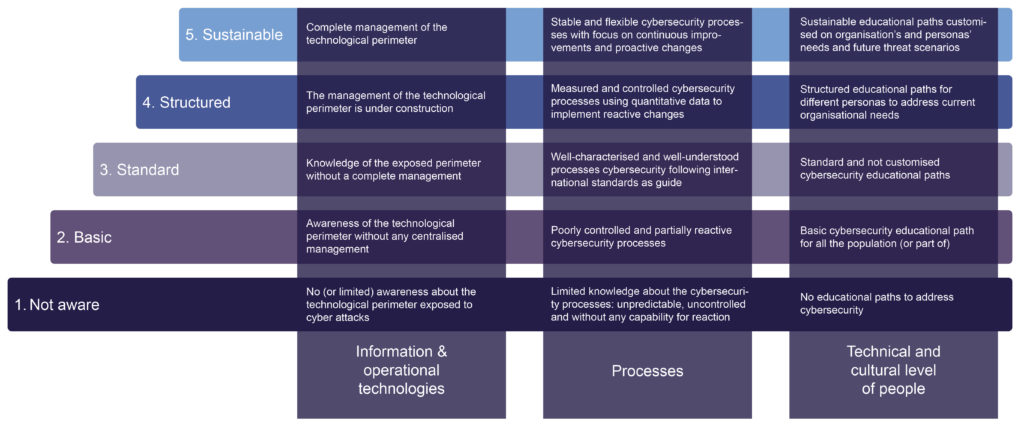
CMM-EP: Cybersecurity Maturity Model for Educational Paths
The CMM-EP as a comprehensive approach
By employing the Cybersecurity Maturity Model for Educational Paths (CMM-EP), organisations can systematically assess the maturity of their cybersecurity scope, particularly in the critical domain of training processes. Therefore, the model describes five levels ranging from “not aware”, representing the rudimentary handling of cybersecurity threats, to “sustainable”, standing for the integration of security-related values and educational pathways.
The CMM-EP assesses companies along three dimensions: Information & operational technologies, processes and the technical & cultural level of people. This evaluation ensures a multidimensional perspective and enables organisations to pinpoint specific areas for improvement.
In essence, the CMM-EP serves as a strategic guide, enabling organisations to navigate through the evolving landscape of cybersecurity threats by finding areas for improvement. Utilising models such as the CMM-EP can help organisations to comprehensively assess and enhance their cybersecurity capabilities.





